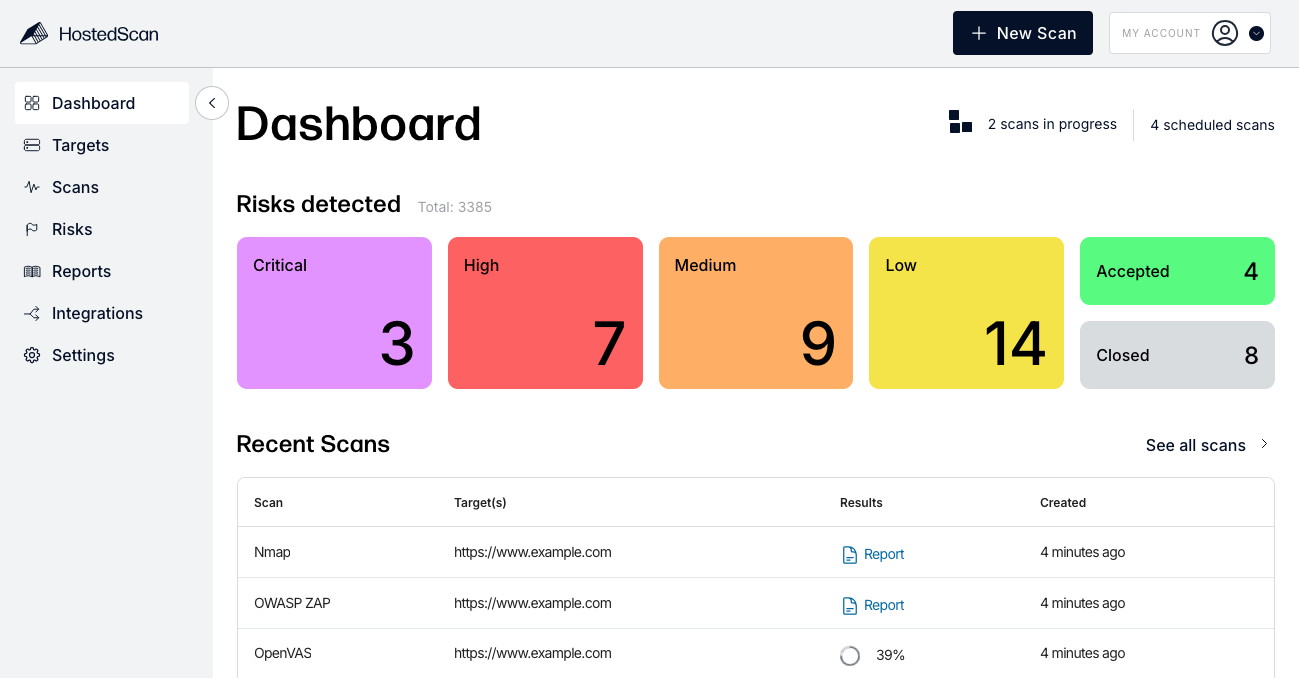
External Vulnerability Scanner
Perform an external vulnerability scan of ip addresses and domains
What is an external vulnerability scanner?
An external vulnerability scanner is software which tests public facing assets, such as public internet ip addresses and domains, for security vulnerabilities. An operator gives the scanner a list of targets and the scanner performs the following steps:
- Discovery: In this phase the scanner makes ping requests and conducts port scans to determine which targets are responding and what ports are open on each target.
- Service detection: Now that the scanner knows what targets and ports are responding, it attempts to determine the actual services that are running. For example: is the target running ssh, snmp, apache webserver, phpmyadmin, etc... To do this, the scanner uses information about commonly used port numbers combined with fingerprinting techniques to verify the service. In many cases, the scanner can even detect the exact software version numbers.
- Vulnerability assessment: Finally, the scanner compiles a list of specific vulnerabilities. In some cases this is as simple as checking the software version numbers that were gathered in the service detection phase against known lists of vulnerabilities, such as the CVE database. In other cases, the scanner makes additional requests to test for the vulnerability, such as testing for unsecured applications or applications using default passwords.
Ready to run an external vulnerability scan?
Run a free scan now to see the power of HostedScan
How to perform a high-quality external vulnerability scan?
There are several important things to be aware of when running an external vulnerability scan. Keeping these in mind will help you achieve significantly better scan results.
- Collect all of your targets: This may seem like a simple step, and it is for some organizations who have a small public facing attack surface area. However, for more complex organizations it's easy to miss an ip address, domain name, or even an entire CIDR block. Anything that is missed won't be scanned.
- Alive check settings: To optimize speed, some scanners will first send a ping request to each target and skip targets which do not respond. This is a check to see if the target is "alive" or "up" and it can save considerable time for very large address spaces. However, in many situations it is better to be thorough and scan anyways as not all targets may respond to ping. Most scanners allow this optimization to be disabled.
- Update the scanner: New vulnerabilities are discovered daily. Most scanners have a feed or database of vulnerability definitions, which should be updated before scanning to ensure that the latest known security issues are checked.
External vulnerability scanning tools
There are several good external vulnerability scanning tools available. Here at HostedScan, we of course recommend our own external vulnerability scanning service. It's transparently powered by open-source tools that are used daily by millions of cybersecurity professionals and we truly believe that it delivers best-in-class quality at a much lower price than the alternatives.
- Average cost savings / year using HostedScan vs the best alternative products
- $3,850 USD
- Average time savings / year using HostedScan vs a do-it-yourself solution
- 438 hours
However, we fully understand if you want to shop around. Some other commonly used commercial offerings are the external vulnerability scans from Qualys, Tenable's Nessus, and Rapid Fire Tools. Alternatively, you can run open source tools yourself, such as OpenVAS/GVM, Nmap, and Nuclei.
A better external vulnerability scanner
HostedScan brings a powerful set of scanning tools together into a comprehensive external vulnerability scanning service for networks, servers, and websites. With HostedScan it's easy and affordable to run industry-trusted scans, triage the results, and generate high-quality reports.