API Security Scan vs Traditional Website Scan
An API vulnerability scan tests API routes for security issues, such as SQL injection and remote command execution (RCE). To understand the API routes and parameters, the scanner reads an API definition file, such as an OpenAPI or Swagger template.
This is different from a traditional website scanner, which starts from a website url and crawls the webpage by following hyperlinks and clicking buttons. While a website scan may discover some APIs while crawling, it will likely be less complete than a scan of the full API definition. However, a traditional website scan will also inspect the website's html and javascript for security issues, such as a vulnerable javascript dependency.
How to set up API security scanning
With HostedScan Security you can import an OpenAPI definition file and scan your API with the OWASP ZAP scanner.
Follow the steps below to set up an API vulnerability scan:
- 01
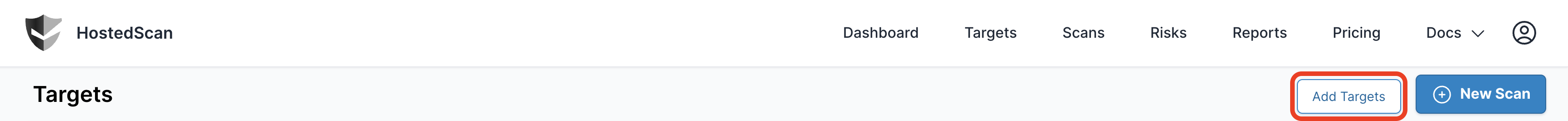
Click the Add Targets button.
- 02
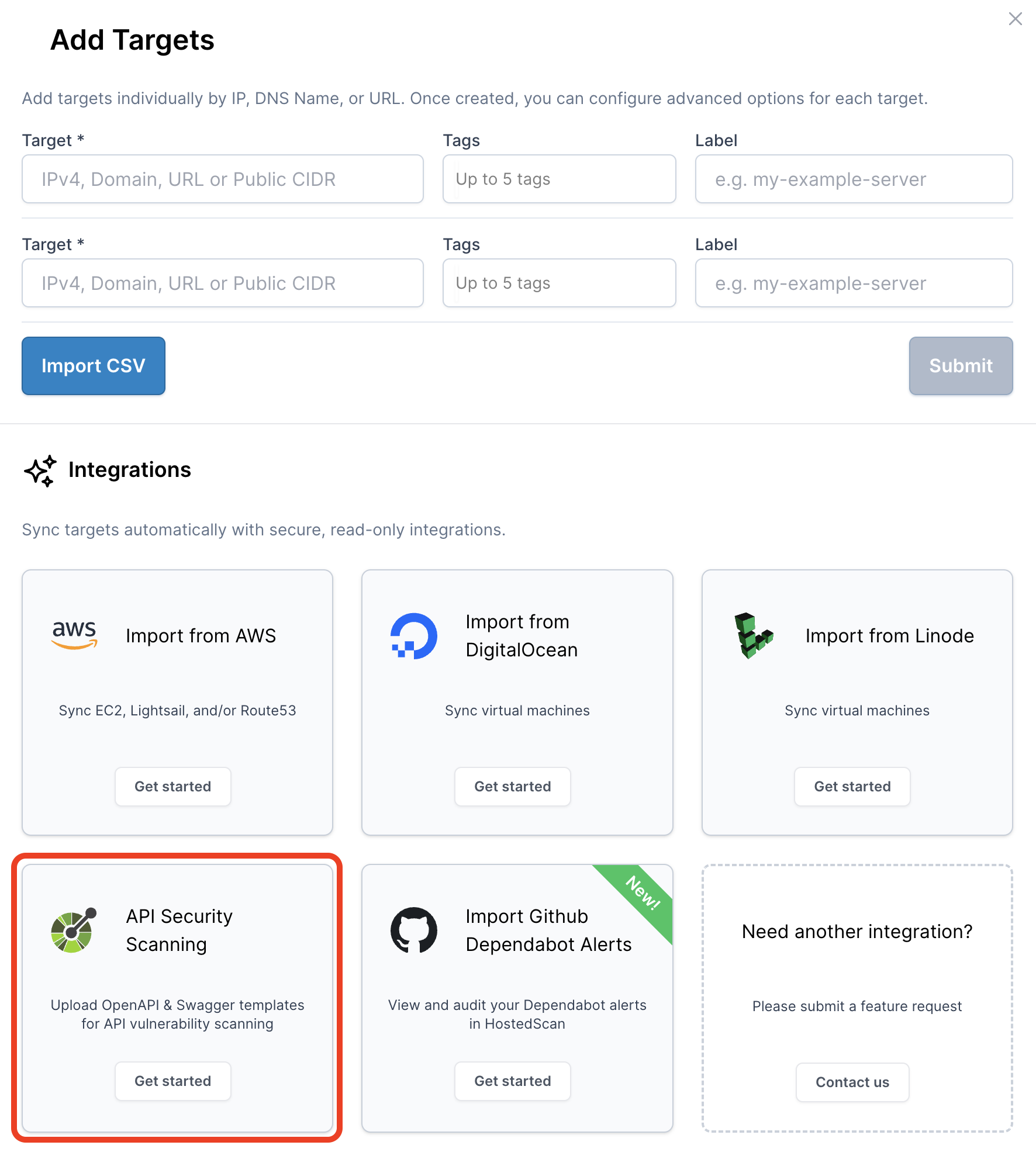
Click the Import from OpenAPI button at the bottom of the
- 03
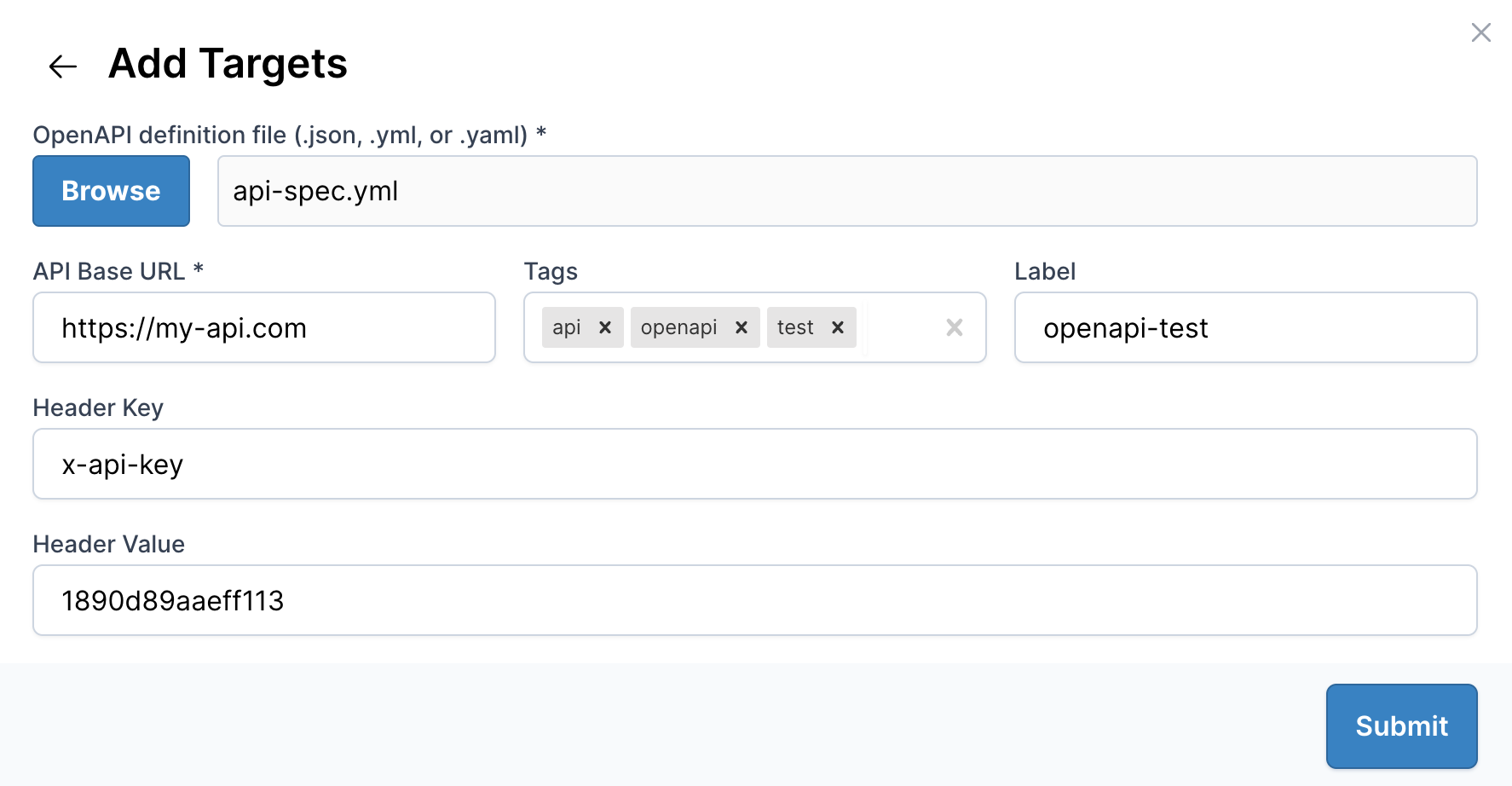
Upload your OpenAPI definition file (JSON or YAML format),
set the base URL, and include headers for authentication (if required).You can configure authentication by setting a Header Key and Header Value with appropiate API keys.
- 04
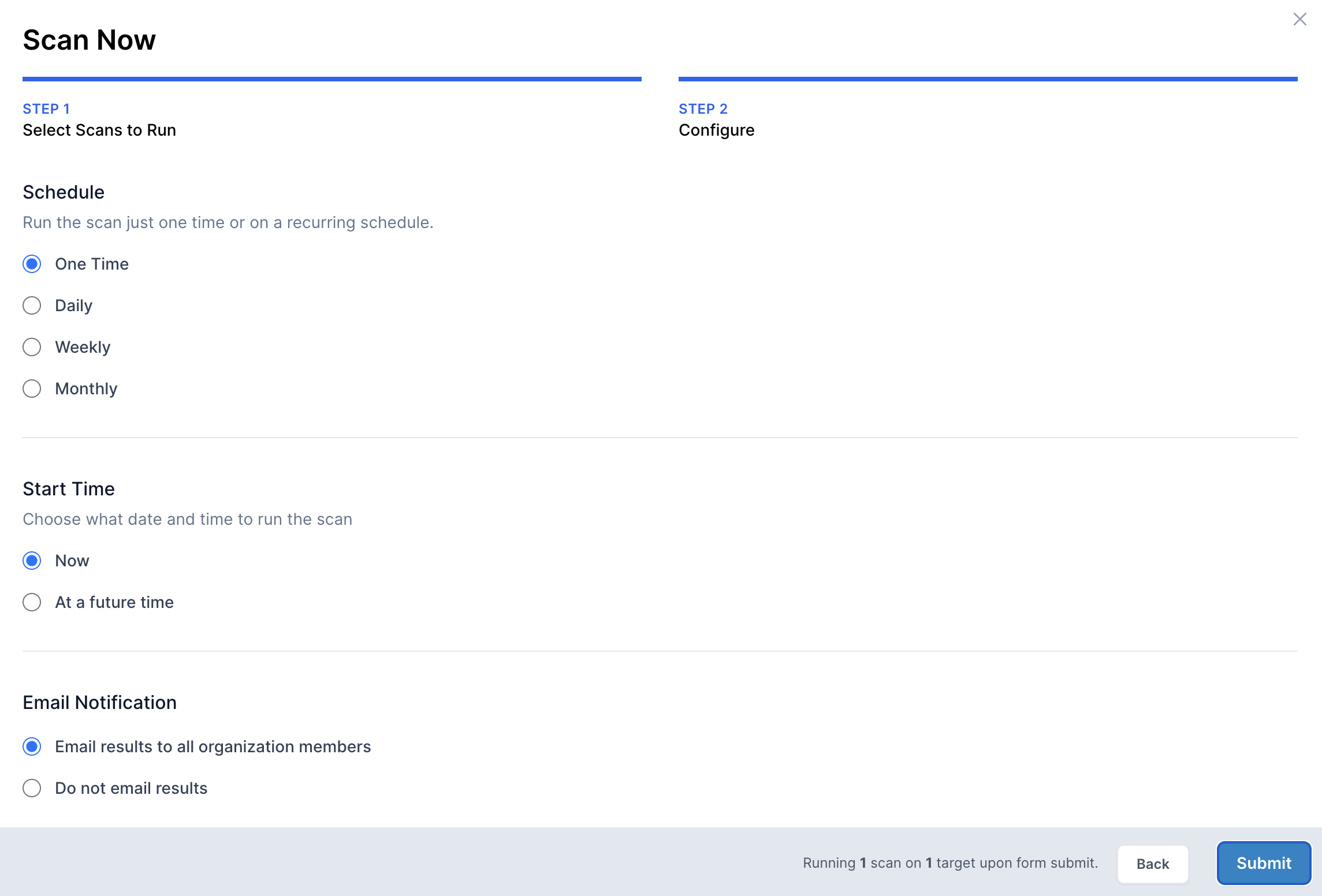
Create a scan for the newly created target.
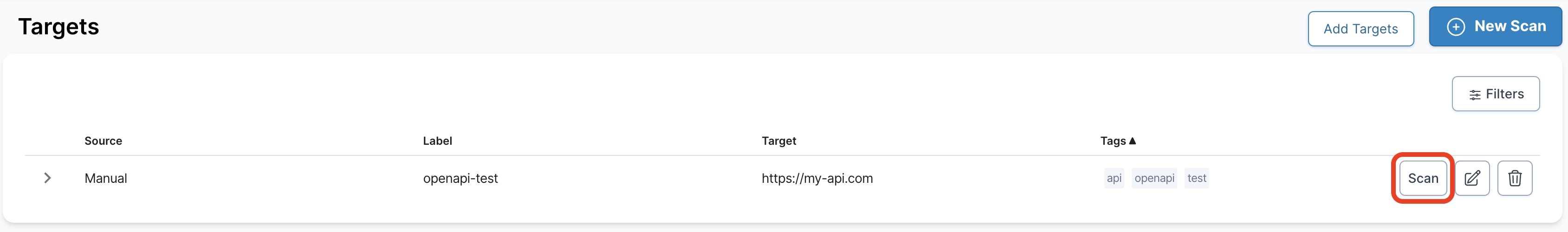
- 05
Run an OWASP ZAP Active scan on the new target.
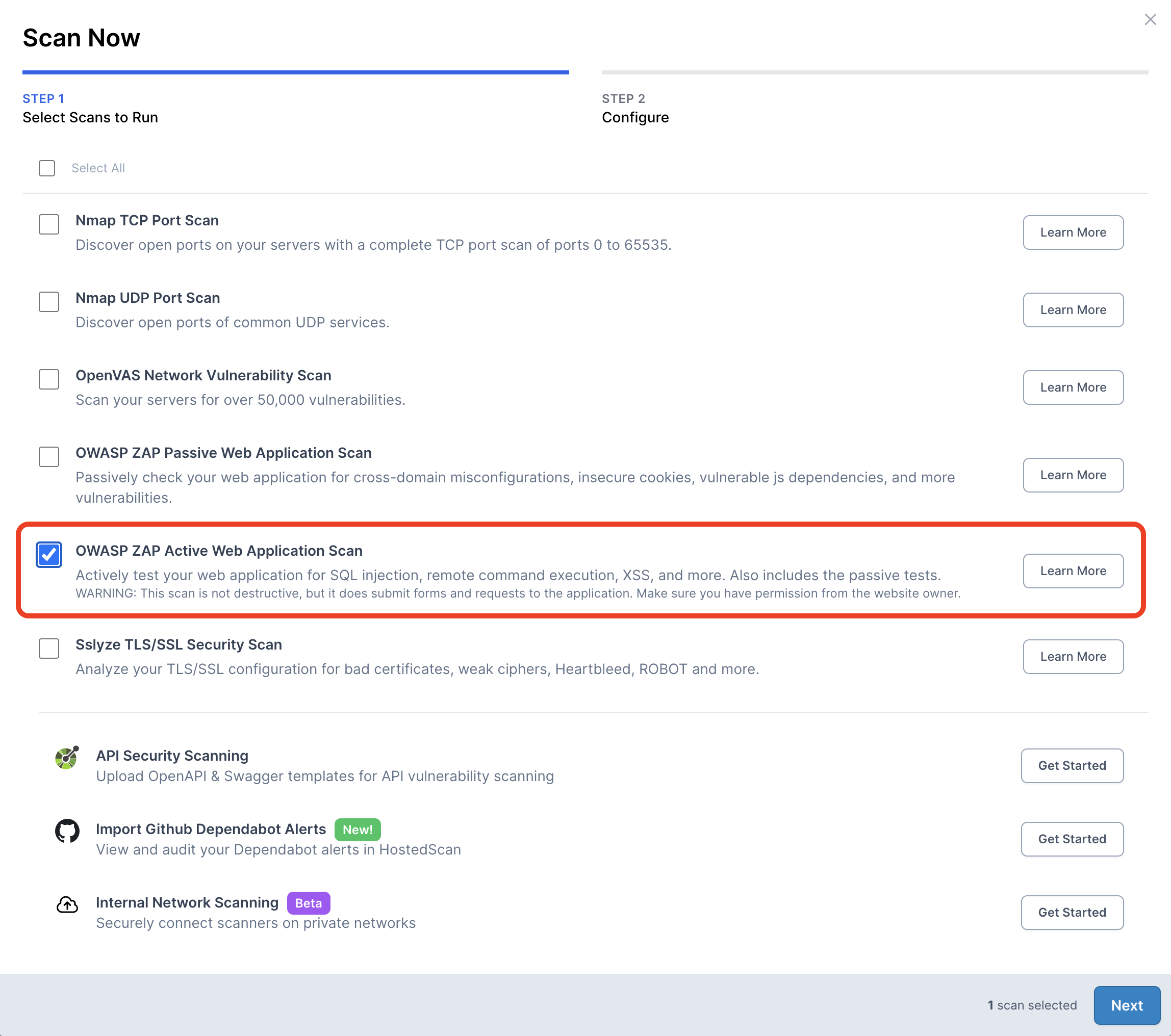
- 06
Finally, configure your scan to either run once or on a recurring schedule, and choose your preferred notification settings.
This scan will send payloads to your API routes