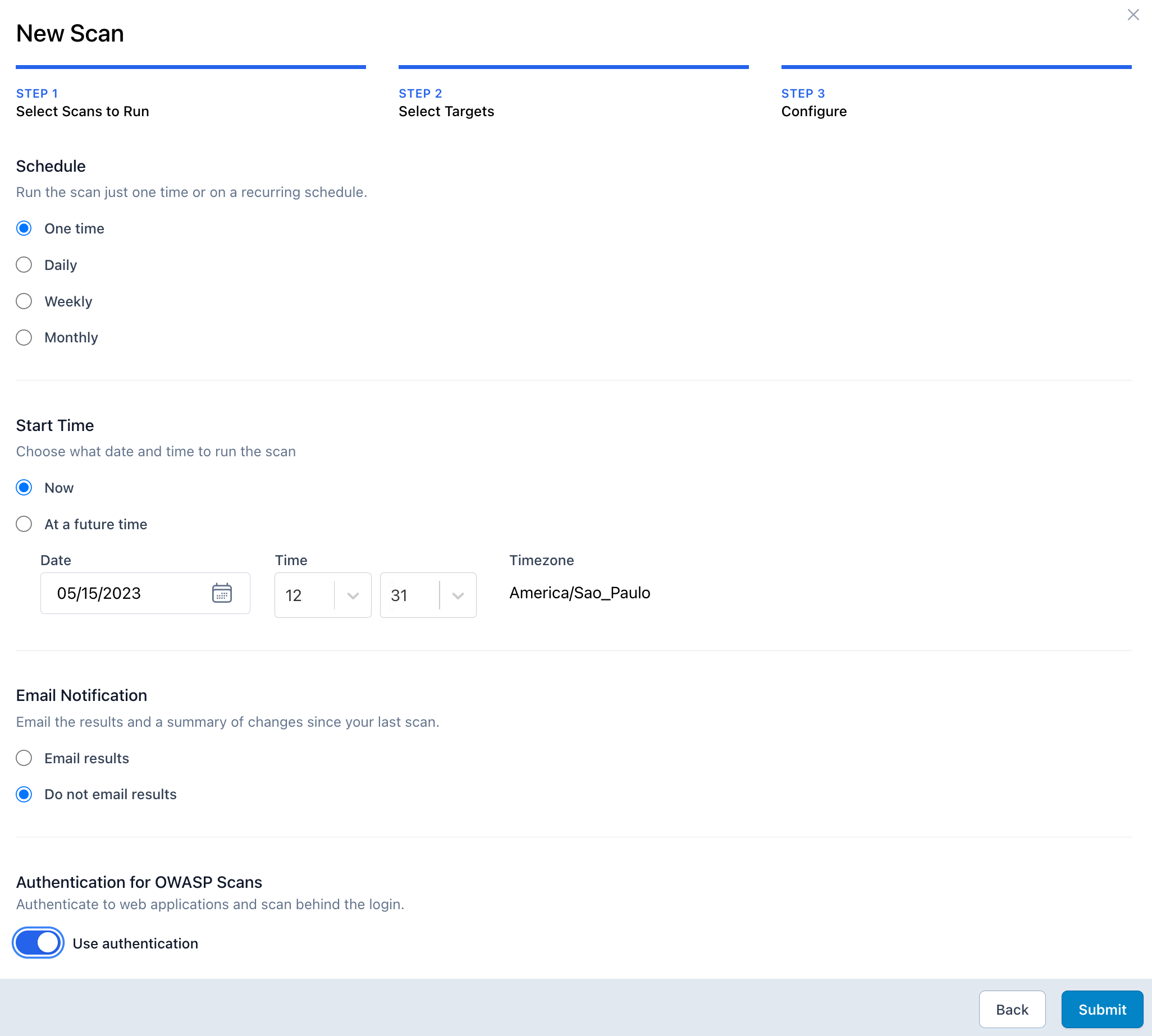
What is an Authenticated Vulnerability Scan?
An authenticated vulnerability scan logs in to the target web application. This allows the scan to cover sections of the application that are accessible only to logged in users. For many web applications, a significant amount of the content is behind a log in and an authenticated scan is required for a thorough security test.
You can authenticate using two methods:
- By creating a selenium script to walk through your login form. Read below for details.
- By configuring customized request headers for alternative authentication strategies like Basic Authentication, Bearer Token and API keys. Read more on Customize Request Headers (OWASP Zap).
How to set up and run an authenticated scan
With HostedScan Security you can easily run authenticated OWASP ZAP scans using a recorded login for your web application. HostedScan uses the recorded login to authenticate into your application and scan behind the login.
Follow the steps below to configure your authentication and run scans.
- 01
Record the Authentication
HostedScan uses Selenium recordings to capture and replay the login steps for a website. Selenium is a widely used open-source tool for recording and automating actions on a web page.
- Install the Selenium IDE browser extension for Firefox or run the Selenium IDE desktop application. The desktop application can be easily launched using a node package manager such as npm: `npx selenium-ide`. Note that the Selenium IDE browser extension is currently not supported in Chrome due to recent changes in Chrome extension requirements.
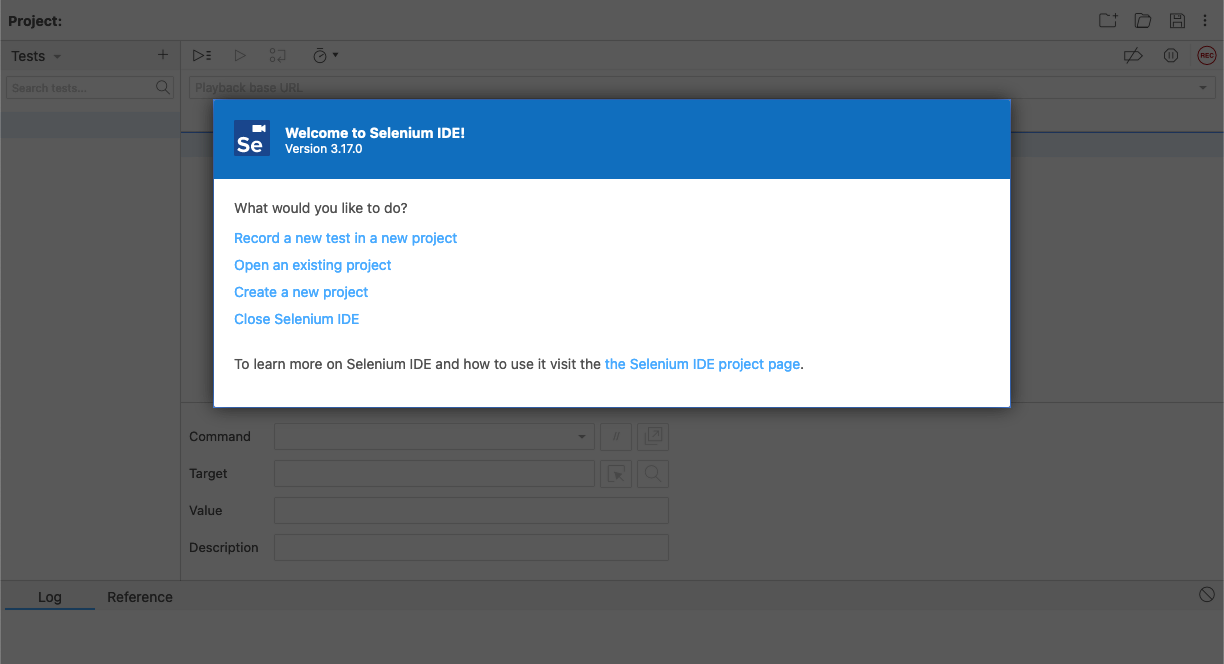
- Open the extension and select Record a new test in a new project, enter a name for the project, enter your website's URL, and then click Start recording.
- Your website will open in a new window where you will make the recording. Authenticate to your website and Selenium will record the actions. Always use a test user account. Some scans will click buttons and submit forms as part of testing, which could cause changes to the account.
- After logging in to your website, stop the recording and save it as a
file..side
- 02
Upload the Recorded Authentication to HostedScan
HostedScan uses Selenium recordings to capture and replay the login steps for a website. Selenium is a widely used open-source tool for recording and automating actions on a web page.
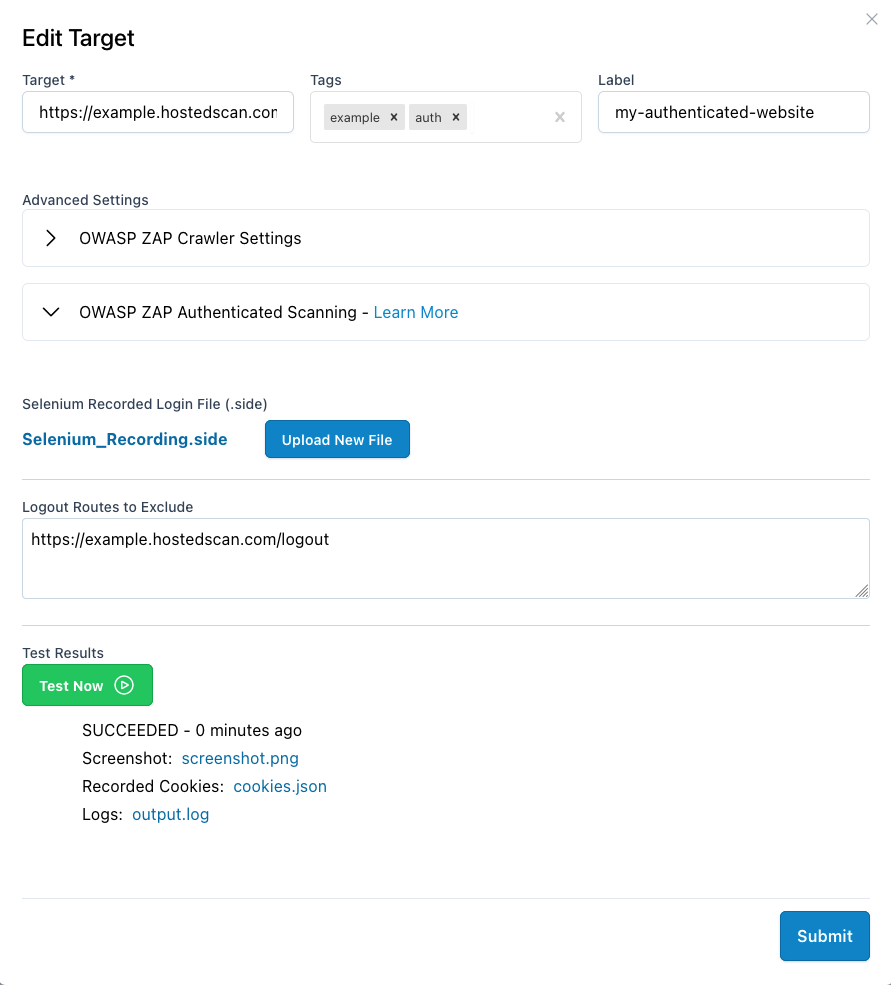
- In your HostedScan account, edit the Target you are configuring for authenticated scanning.
- Click Upload New File and upload the .side file that you previously recorded with Selenium.
- Under Logout Routes to Exclude, list the logout URLs for your application. e.g.
. It is important to configure these URLs so that the scanner does not visit them and unauthenticate during the scan.https://mysite.com/logout - Test your configuration by clicking >> Test Now. This will test if we can playback your Selenium recording. When the test is finished, verify that the captured screenshot shows your website authenticated as you expect.
- 03
Run Scan!
On the Targets menu click the New Scan button.
The scan may take a couple minutes to start as it goes through the authentication process.
- 04
Select an OWASP ZAP Active Web Application Scan.
- 05
Select your Target.
- 06
Select the option to enable authentication (where you select schedule and email settings) and click "Submit"