What is continuous security monitoring?
Continuous security monitoring is the process of constantly evaluating your IT assets for cybersecurity threats. To successfully set up continuous monitoring requires a few pieces:
- Frequent vulnerability scanning.
- Alerting for any new threats discovered during scanning.
- Risk vulnerability management tools to prioritize fixes and track false positives.
- A standard operating procedure (SOP) defining how you will respond to new threats.
Continuous vulnerability scanning vs penetration testing
Traditionally, companies perform an annual penetration test. This penetration test is a one-time service provided by a cybersecurity contractor. While the penetration test is a valuable part of a business' cybersecurity strategy, an annual test is too slow to protect against new vulnerabilities. In 2021, there were 20,149 new CVEs reported. More frequent vulnerability scanning is required to protect against these emerging threats.
It is also the case that modern software development teams move very quickly. Your software architecture and code may change substantially in one year. Each change can introduce regressions or new security risks. Continuous vulnerability scanning will help you find and fix these issues before they can be exploited.
HostedScan's continuous vulnerability management tools
HostedScan Security provides powerful continuous vulnerability management tools to protect your business:
- Vulnerability scans on a monthly, weekly, or daily schedule.
- Email alerts for any new findings.
- Dashboards and reporting.
- Sharing and collaboration with team accounts.
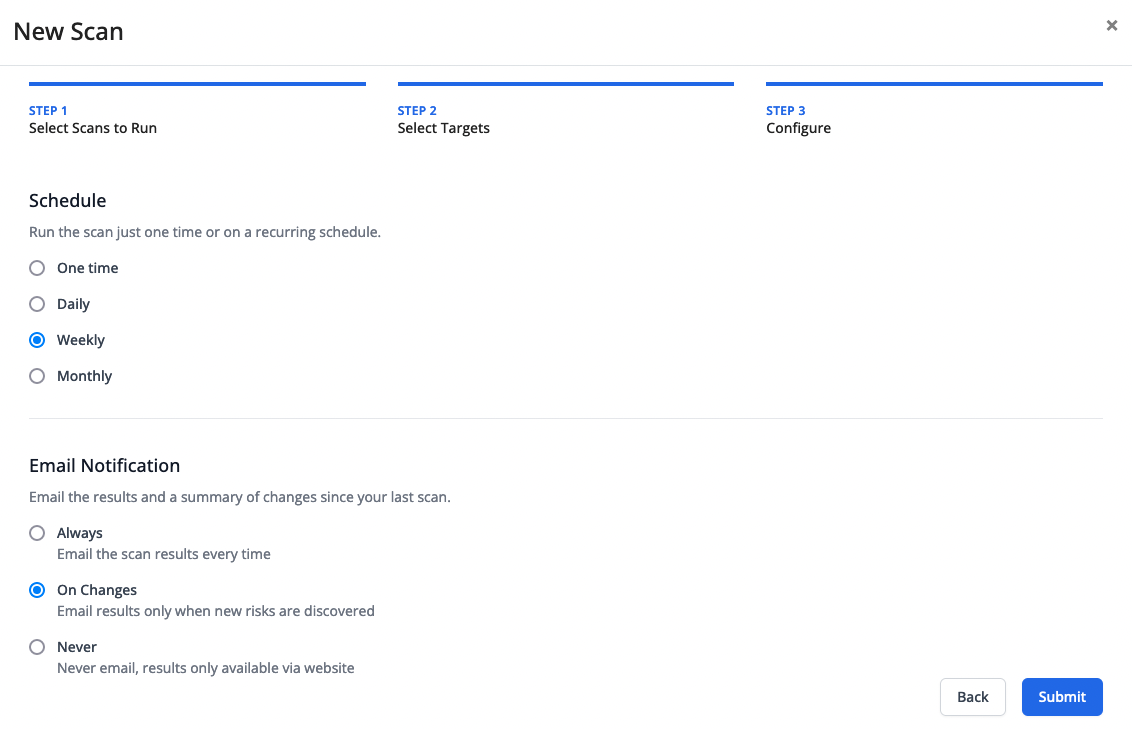
Example Scheduled Vulnerability Scanning Configuration