What are advanced acceptance rules for risks?
Not all risks are threatening, in fact, some risks are acceptable. Port 80 and port 443 are frequently open by design for any webserver. A timestamp disclosure in a piece of javascript may not matter at all. It's in these cases that you might want to mark a risk as acceptable.
HostedScan provides two ways of marking a risk as acceptable:
- You can accept a specific risk for a specific target. This is the easiest and simplest way to accept a risk.
- You can craft a condition that spans across targets, across risks, to specify a whole class of risks as acceptable.
This second case is where advanced acceptance rules are created. These rules let you control the fine-grained criteria for when a risk might be accepted, or even automatically accept potential risks that may be discovered so long as they meet your criteria.
Example advanced acceptance rules for risks
To get an idea of when you might want to do this, here are some good examples we have seen:
- Accept ephermal open port risks generated on a load balancer
- Automatically accept ports 80 and 443 on any target tagged as a webserver
- Automatically accept low threat risks generated by a particular scanner as not priority
- Accept certain instances of a cookie having a less than ideal configuration
How to setup an advanced acceptance rule for risks
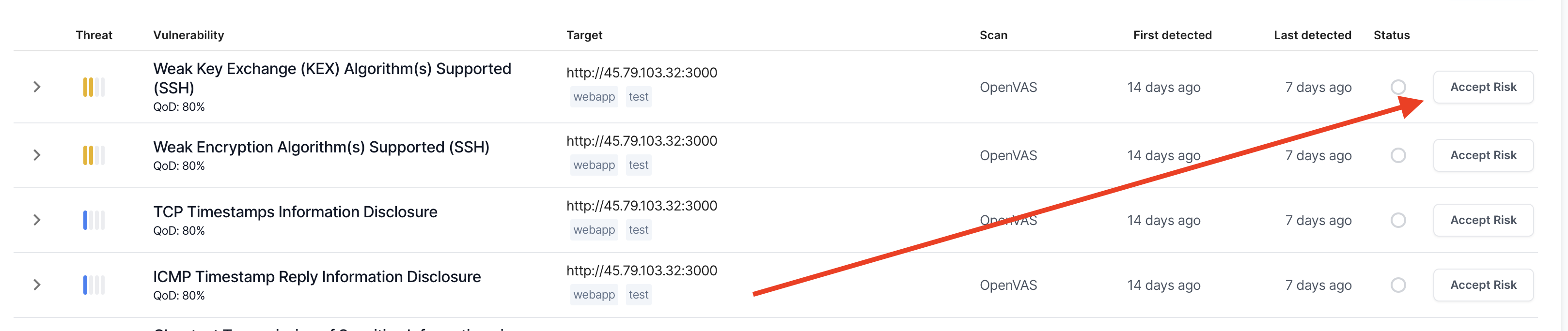
- 02
Accept risk, or expand editor
With the accept risk rule editor, you have a choice to make:
- Accept the current risk and target pair.
- Expand the editor to create an advanced rule.
If you're fine with choice one, hit the Accept button. If you would like to do something more advanced expand the Advanced Rule Editor section.
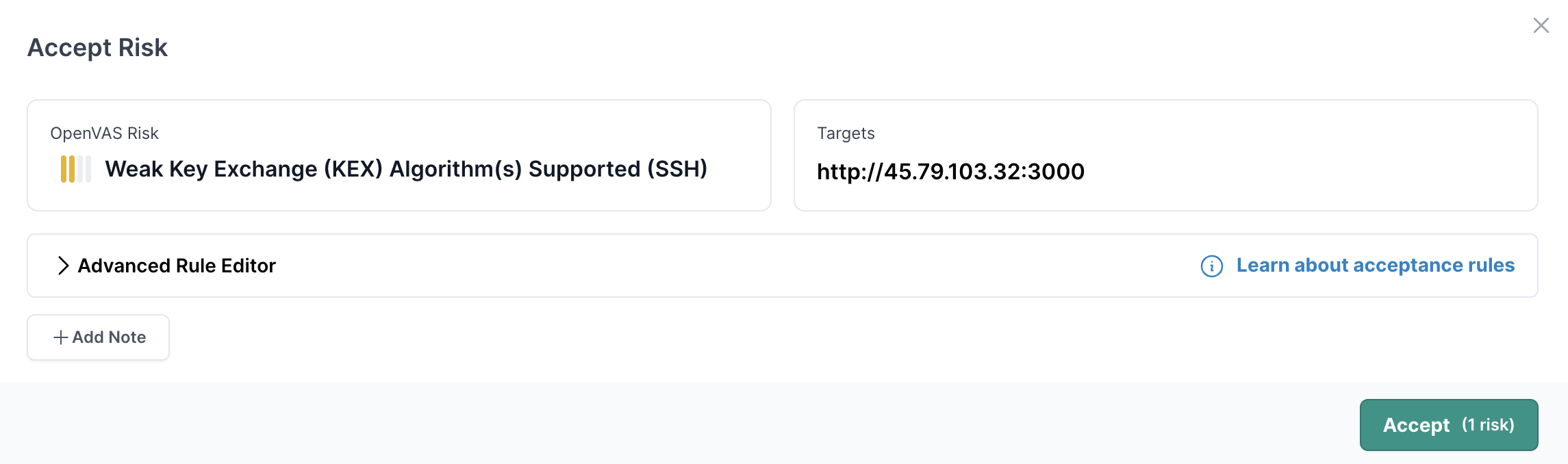
- 03
Understanding the acceptance conditions
The code editor allows crafting any arbitrary query to match against your total set of risks. The query is structured in a JSON format. The query is composed of Mongoose like operators, formatted similarly to a mongoose query.
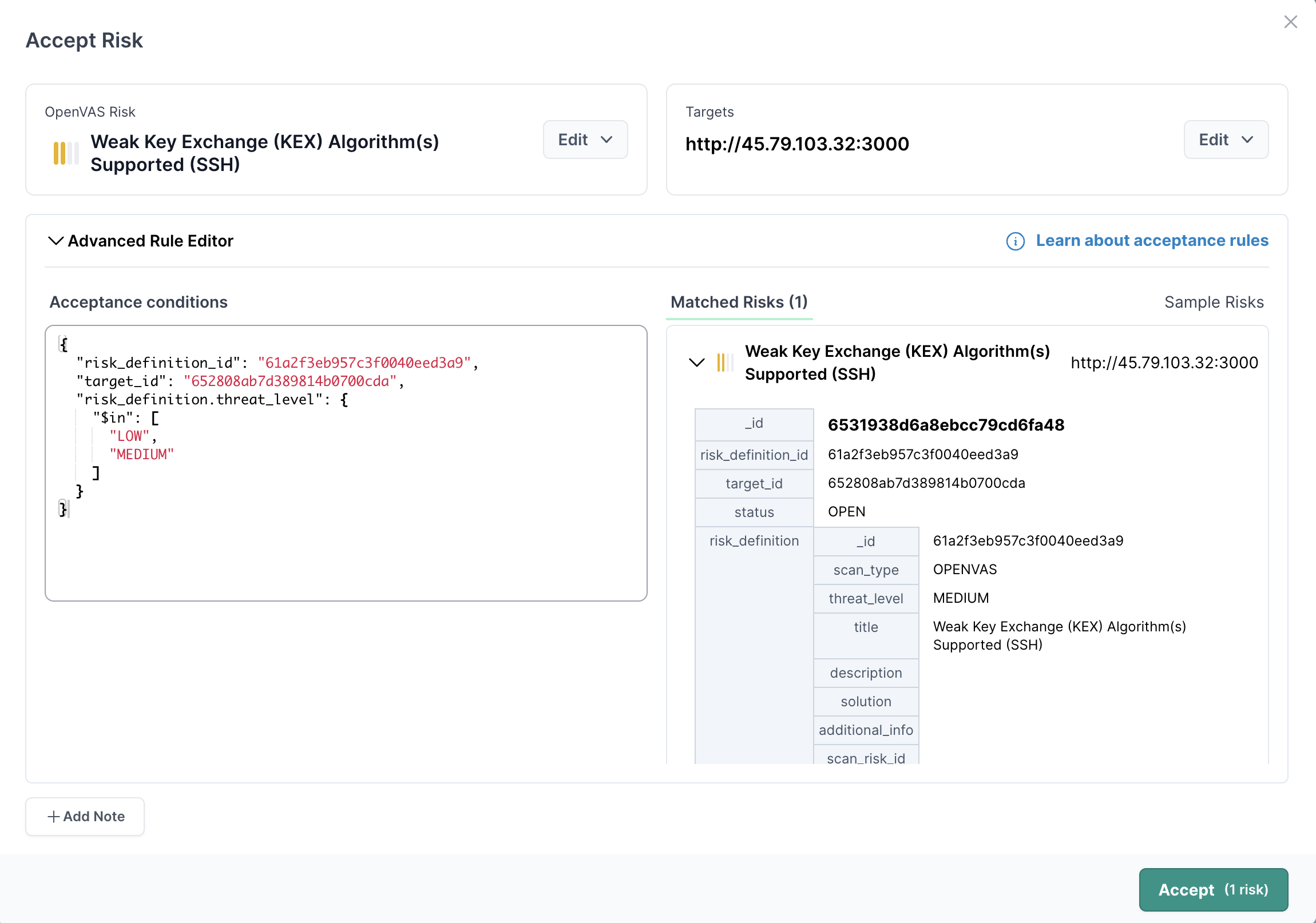
Try these three steps to familarize yourself
- Click on the matched risk in the left hand pane to expand it and view the various properties you can match against.
- Click on one of properties in the value of one of the properties, like MEDIUM for the threat level. This will be automatically added the property and value as a condition in the editor.
- Modify the query in the editor to use an operation, in this case we have added the $in operator and chosen two values
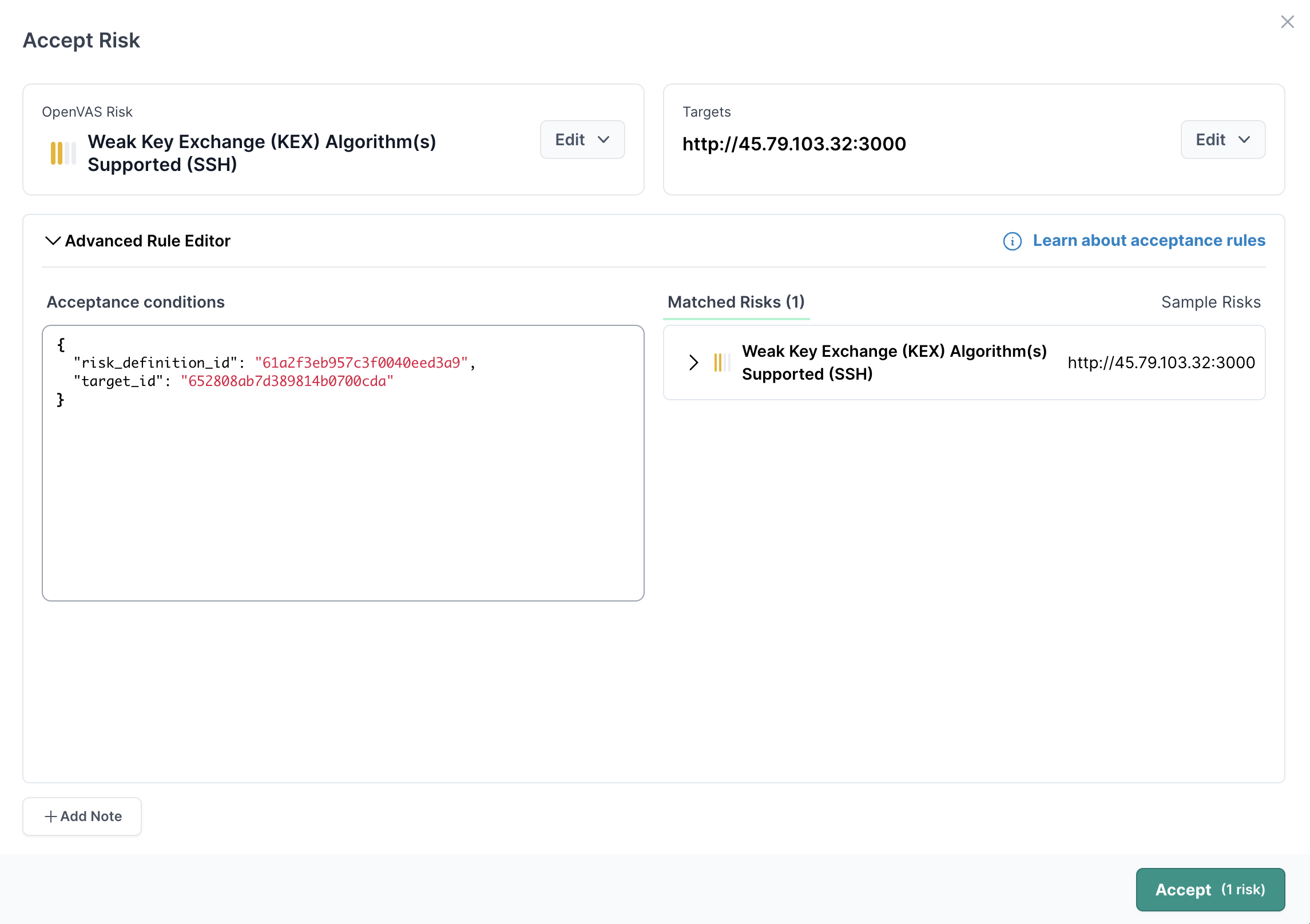
- 04
Craft a risk acceptance rule
With advanced rule editor open you will see a couple of options:
- On the top row Edit buttons appear next to the risk and target
- On the left side of the pane, a code editor is populated with the specific risk definition and target ids corresponding to the current risk and target selected.
- On the right side of the pane, a list of risks that match the criteria in the editor pane is shown.
The edit buttons along the top row help to quickly change the risk selected, and the targets selected. Try using these buttons, and see how the code in the editor changes, along with the Matched Risks list.
- 05
Operators for acceptance rules
The operators roughly match what is available for MongoDB queries
The following operators are available to use for writing a query to match risks for acceptances:
Operator Type Description $all array requires all values in the array to be values in the property as well. Used on properties that are also an array. { "$all": ["prod", "webserver"] } $and array requires an array of expressions to all be true $elemMatch object takes an expression and checks that an element on the property matches the expression. I.e. { "$elemMatch": { "port": } } $eq any the property matched equals the value in the query $exists boolean the property checked needs to exist if "true", otherwise reject values that do not exist using "false" $gt number or string the property checked needs to be greater than the value in the query $gte number or string the property checked needs to be greater than or equal to the value in the query $in array the property matched needs to be one of the values $in the array for the query $lt number or string the property checked needs to be less than the value in the query $lte number or string the property checked needs to be less than or equal to the value in the query $mod array the modulus of the property is equal to the value. I.e. [4, 0] means "the property modulus 4 equals 0" $ne any the property matched does not equal the value in the query $nin array opposite of $in, the property matched must not be one of the values in the array for the query. $nor array opposite of OR: { $nor: [{ _id: "12345" }, { _id: "67890" }] } $not object Not a given expression. I.e. { "$not": { "$size": 3 } } $or array OR array of expressions $size number the property array matches the length specified in the value in the query $regex string or regular expression the property matches the given regular expression